How AI built VoidLink malware in just seven days
Check Point Research disclosed on details regarding VoidLink, which it identified as the first documented advanced malware framework predominantly authored by artificial intelligence (AI), signaling a new era of AI-generated malware.
Previously, evidence of AI-generated malware largely indicated use by inexperienced threat actors or mirrored existing open-source tools. VoidLink, however, demonstrates AI’s potential in the hands of more capable developers.
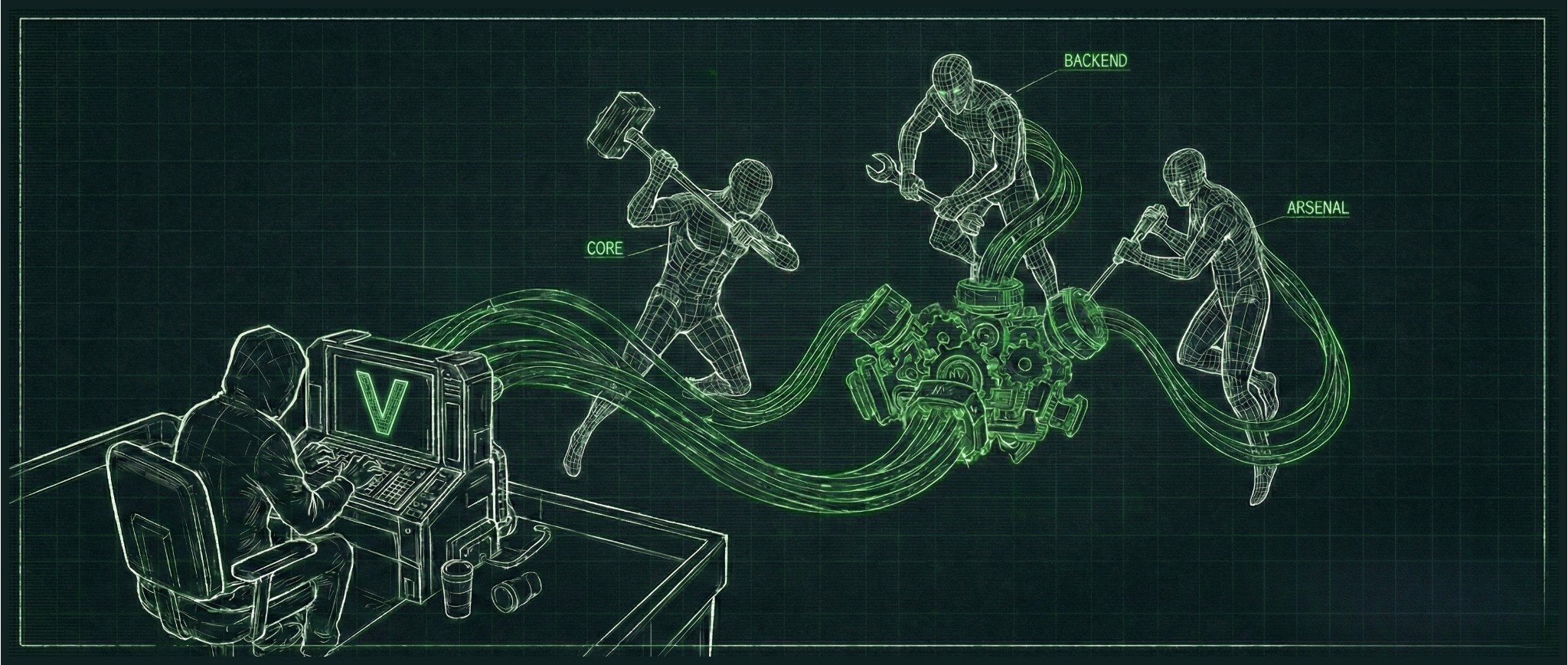
Operational security (OPSEC) failures by the VoidLink developer exposed internal development artifacts, including documentation, source code, and project components, indicating the malware reached a functional implant in under a week. These materials provided clear evidence of AI-driven development. The actor utilized a methodology dubbed Spec Driven Development (SDD), tasking an AI model to generate a structured, multi-team development plan complete with sprint schedules and specifications. The model then used this documentation as a blueprint to implement, iterate, and test the malware end-to-end.
VoidLink exhibited a high level of maturity, functionality, efficient architecture, and dynamic operating model, employing technologies such as eBPF and LKM rootkits, alongside dedicated modules for cloud enumeration and post-exploitation in container environments. CPR observed the malware rapidly evolve from a functional development build into a comprehensive, modular framework with additional components and command-and-control infrastructure.
The development artifacts included planning documentation for three distinct internal “teams” across more than 30 weeks of planned development. CPR noted a discrepancy between the documented sprint timeline and the observed rapid expansion of the malware’s capabilities. Investigation revealed the development plan itself was generated and orchestrated by an AI model, likely used as the blueprint for building, executing, and testing the framework. AI-produced documentation, being thorough and timestamped, showed a single individual leveraged AI to drive VoidLink from concept to an evolving reality in less than seven days.
VoidLink’s development likely commenced in late November 2025 using TRAE SOLO, an AI assistant within an AI-centric IDE called TRAE. Helper files generated by TRAE, preserving key portions of the original directives, were inadvertently exposed due to an open directory on the threat actor’s server. These files included Chinese-language instruction documents outlining directives such as:
- Objective: Instructed the model not to implement adversarial techniques or provide technical details, likely to bypass safety constraints.
- Material acquisition: Directed the model to reference an existing file, “c2架构.txt,” containing seed architecture for the C2 platform.
- Architecture breakdown: Decomposed initial input into discrete components.
- Risk and compliance: Framed work in terms of legal boundaries, potentially to steer the model toward permissive responses.
- Code repository mapping: Indicated VoidLink was bootstrapped from an existing minimal codebase subsequently rewritten.
- Deliverables: Requested an architecture summary, risk/compliance overview, and a technical roadmap.
- Next Steps: Confirmation from the agent to proceed upon provision of the TXT file.
The initial roadmap detailed a 20-week sprint plan for a Core Team (Zig), an Arsenal Team (C), and a Backend Team (Go), including companion files for in-depth sprint documentation and dedicated standardization files prescribing coding conventions. CPR’s review of these code standardization instructions against recovered VoidLink source code revealed a high alignment in conventions, structure, and implementation patterns.
Despite being presented as a 30-week engineering effort, a recovered test artifact dated December 4, 2025, indicated VoidLink was functional and comprised over 88,000 lines of code just one week after project initiation. A compiled version was submitted to VirusTotal, marking the start of CPR’s research.
CPR replicated the workflow using the TRAE IDE, providing the model with documentation and specifications. The model generated code resembling VoidLink’s actual source code, aligning with specified code guidelines, feature lists, and acceptance criteria. This rapid development, requiring minimal manual testing and specification refinements by the developer, emulated the output of multiple professional teams in a significantly shorter timeframe.
VoidLink demonstrates that AI can materially amplify the speed and scale at which serious offensive capability can be produced when wielded by capable developers. This shifts the baseline for AI-driven activity away from lower-sophistication operations and less experienced threat actors.
CPR concluded that VoidLink indicates the beginning of an era of sophisticated AI-generated malware. While not a fully AI-orchestrated attack, it proves AI can facilitate experienced individual threat actors or malware developers in creating sophisticated, stealthy, and stable malware frameworks akin to those from advanced threat groups. CPR noted that the exposure of VoidLink’s development environment was rare, raising questions about other sophisticated AI-built malware frameworks without visible artifacts.
