Devious ‘man in the middle’ hacks on the rise: How to stay safe
In the old days, anyone could easily snoop on internet traffic. The data was unprotected, so everything getting passed between a computer and a server was out in the open, whether that was website text and images or your username and password. When universal encryption took over, it blocked spying—but unfortunately, bad actors evolved along with the increased security.
One kind of attack is especially popular: First known as a man-in-the-middle attack (now referred to machine-in-the-middle, adversary-in-the-middle, or on-path attacks), it lets hackers insert themselves between your devices and the server they communicate with, in order to steal login information ad session cookies to then take over your account.
It starts with you clicking on a phishing link, then entering your credentials on a fake copy of a legitimate website. Bad actors then capture the username and password, along with the access token, then redirect you to the real website.
MitM attacks can be used on accounts with strong, unique passwords and even locked down with two-factor authentication (2FA), as recently popped up in the news when Google and Microsoft accounts became targets of a new phishing kit. (Yep, even hacking can be as simple as a software subscription.)
But as unnerving as it can feel to know that hackers can “defeat” 2FA, you’re not defenseless against an MitM attack. In fact, you can strengthen your security with a simple change in how you login—though you can do a couple of other things to help, too.
Use a passkey


When passkey support began rolling out widely last year, experts heralded them as a huge step up in security—for good reason. They’re easier to use than passwords, and they can’t be stolen in phishing attacks (ahem). Against MitM attacks, a passkey is one of the strongest defenses available.
All you need is a device like a smartphone, PC, or hardware key. You can also use a password manager that supports passkey storage. For each website, your device will create a unique passkey, which is made up of two encryption keys—one public and one private. The public key gets shared with the website, while the private key stays protected on the device. No one can guess the private key based on the public key. And relevant to MitM attacks, a passkey only works with the site it’s created for. At login, the website will send a prompt to your device, asking for permission to authenticate through the passkey. All you need to do is grant permission by entering a PIN or using biometrics (e.g., fingerprint or facial recognition).
Many major websites now support passkeys, including Google, Microsoft, and Apple—accounts that can be highly dangerous to lose control of. (Our guide for setting up passkeys on a Google account gives a general idea of how to get started overall.) In fact, when asked for comment on the latest MitM attack targeting Gmail accounts, Google mentioned passkeys as a way to reduce vulnerability to such attacks.
The main downside to passkeys is that if you lose your device, you can lose access to the passkey, so having backups is important.
Use stronger two-factor authentication

Alaina Yee / Foundry

Alaina Yee / Foundry
Alaina Yee / Foundry
Even with the introduction of passkeys, passwords haven’t disappeared yet—not by a long shot. Most websites with passkey support still keep your password on file. And of course, some sites have yet to implement passkeys.
In both cases, two-factor authentication (2FA) should still be a first move to counter MitM attacks. Not all such campaigns circumvent 2FA just yet, and for those that do, 2FA doesn’t become completely useless—it just narrows what types still work. Codes sent over SMS (or email) or generated by an app can be stolen, but hardware keys using protocols like FIDO2 operate similar to passkeys. For authentication to work, the request must come from the trusted domain. Any others won’t get the same data during the exchange.
Security keys do cost money, however. For example, a basic YubiKey (a popular brand of hardware keys favored by security enthusiasts) starts at $25, and goes up to as much as $75 for ones with wider 2FA protocol support and connection types. And like passkeys, if you lose the device with no backups, you’ll land in a tough spot.
Avoid phishing links

Tech Advisor

Tech Advisor
Tech Advisor
Sometimes, the best solution to a problem is to cut it off at its source. In the case of MitM attacks, you can achieve this by steering clear of phishing links (and sites).
It’s a common sense approach, but it’s not always possible to nail it perfectly. You can stumble upon a phishing website in multiple ways: Maybe you mistype a url. You click on an malicious advertisement. You don’t look closely enough at an email or text message. And even if you’re not distracted or in a rush, AI chatbots can now help non-native speakers polish up the messages that accompany phishing links, making phony URLs harder to spot.
But you can still avoid them. Refinements in your behavior help. Get an unsolicited message asking you to log into your account or change your password? Open a fresh tab and navigate directly to the site. Not sure if you’re on the correct site? Scrutinize the address before clicking around or filling out any forms. Want to ensure you’re selecting an actual search result? Use an ad-blocker to keep sponsored results from appearing. Hopping on public Wi-Fi? Fire up your own personal hotspot, or at least use a VPN so no one can manipulate your traffic.
Our Favorite antivirus Norton 360 Deluxe Read our review
Price When Reviewed:
$49.99 for the first year
Best Prices Today:
$19.99 at PCWorld Software Store |
$49.99 at Norton
Read our review
Price When Reviewed:
$49.99 for the first year
Best Prices Today:
$19.99 at PCWorld Software Store |
$49.99 at Norton
But software can also assist you. Antivirus is a main line of defense, be an independent security suite or Microsoft’s native Windows Security tools. These apps now automatically screen for shady websites while you browse and download email, and will block known malicious URLs. Modern browsers like Google Chrome and Mozilla Firefox have security protections baked in too, though limited to just web browsing. And browser extensions from major antivirus vendors can both stop you from visiting a bad site and label search results with icons indicating if they’re safe or not.
Additional protection is on the way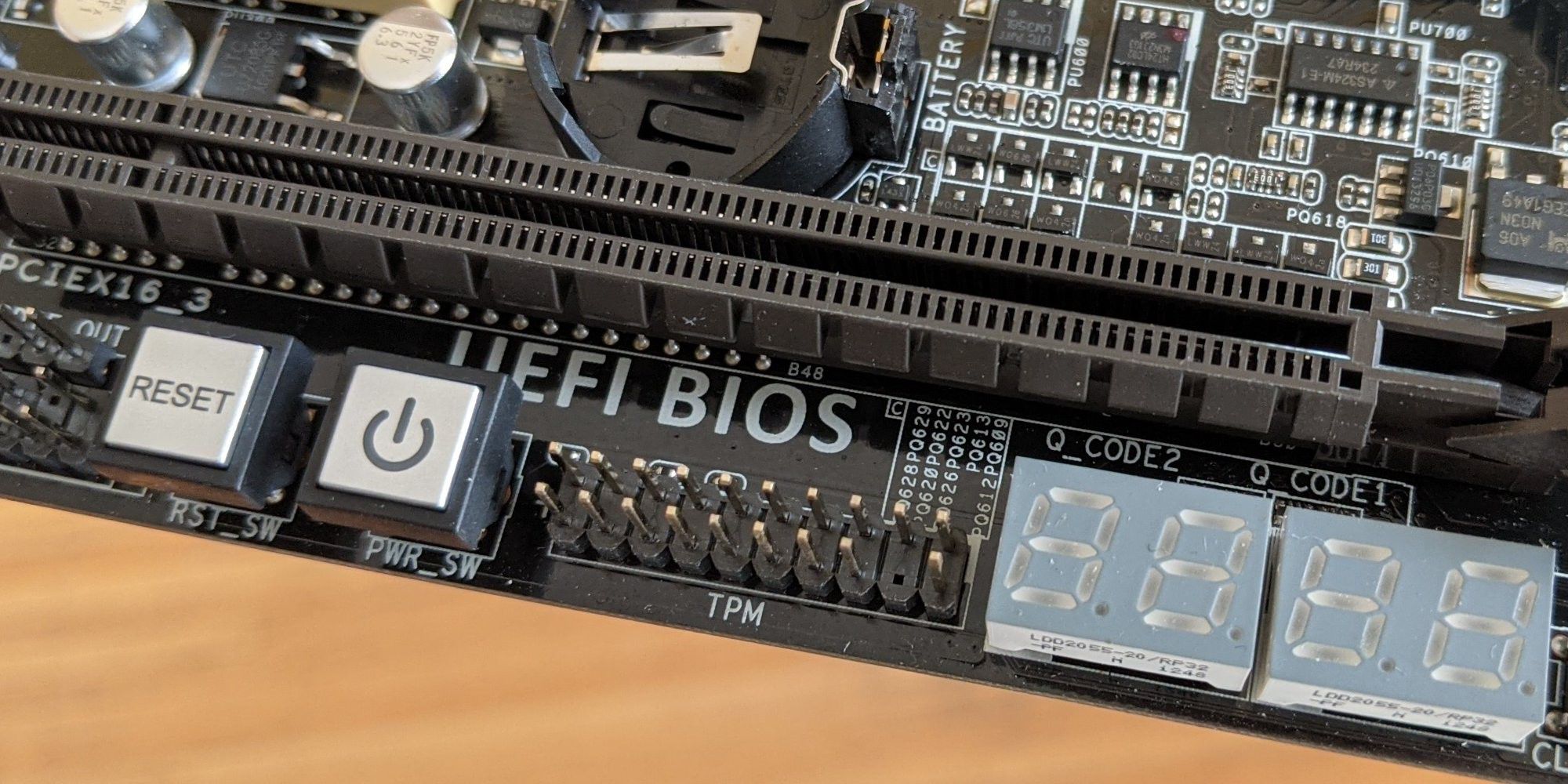 On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.
On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.
 On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.
On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.IDG
 On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.
On this motherboard, you can install a physical trusted platform module—but these often aren’t necessary on modern PCs, since recent AMD and Intel CPUs have firmware TPM.IDG
IDG
Changing to passkeys, upgrading your two-factor authentication method, and staying hypervigilant can eat valuable time. Google is looking to ease that burden with a new tool Device Bound Session Credentials (DBSC), which would capture additional information about the device you’re using when establishing a browsing session. Such a move would make stealing access tokens harder.
Similar to passkeys and two-factor authentication hardware keys, DBSC relies on public-key cryptography (a public/private key pair). On a PC, the device creating the public/private key pair would be its Trusted Platform Module, or TPM—the very type of module required by Windows 11. Because the session is inextricably linked to that TPM, attackers shouldn’t be able to use hijacked credentials to log in to your accounts. At least, not remotely; a hacker would need to plant a malicious app on a system, which is easier for antivirus (and corporate IT departments closely monitoring employee devices) to spot.
DBSC is being developed as open source, with the aim to universally strengthen web standards. Each session-device pairing is unique, so privacy should be less of a concern even with Google driving the project. Currently, DBSC has entered an early trial phase within Chrome, with a broader public trial planned for the end of 2024. Other interested companies already include Microsoft as well as Okta, a major IT service management company.
Antivirus, Personal Software, Security Software and Services